Thursday, 5 January 2012
How to inject code into a exe file
Do you like this story?
*** THIS TUTORIAL IS ONLY FOR EDUCATIONAL PURPOSES!***
-Requirements-
At first we need a debugger. I prefer OLLYDBG(the best debugger on earth :P)
At twice we need a target application to inject our code.
I will take the windows NOTEPAD.EXE .
Make a copy if this EXE in a new folder named CodeInjectTest.
Thats all ;)
At first we need a debugger. I prefer OLLYDBG(the best debugger on earth :P)
At twice we need a target application to inject our code.
I will take the windows NOTEPAD.EXE .
Make a copy if this EXE in a new folder named CodeInjectTest.
Thats all ;)
In our case we'll inject a simple MessageBox at Notepads start.
Start up Notepad now and validize that Notepad is the original one.

If you're sure now that's the original Notepad open the Notepad.exe with Olly.
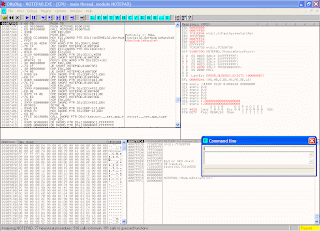
Yuppi! If you're ready you get this window:
Because we're going to inject some code we've to have some space to inject it.
In a EXE file are a lot of CodeCaves were nothing is done (DB 00).
So lets scroll the CPU window a little bit down until you find a CodeCave(look below).
Do you see the red box I've drawn for you? ;) THIS is a CodeCave!
Here we can inject some custom code without interfering the programs flow.
If you know the API call for a MessageBox you don't need to
read this lines.
Yuppi! If you're ready you get this window:
Because we're going to inject some code we've to have some space to inject it.
In a EXE file are a lot of CodeCaves were nothing is done (DB 00).
So lets scroll the CPU window a little bit down until you find a CodeCave(look below).
Do you see the red box I've drawn for you? ;) THIS is a CodeCave!
Here we can inject some custom code without interfering the programs flow.
If you know the API call for a MessageBox you don't need to
read this lines.
***** START QUOTE FROM THE WIN32 PROGRAMMERS REFERENCE
The MessageBox function creates, displays, and operates a message box.
The message box contains an application-defined message and title,
plus any combination of predefined icons and push buttons.
The MessageBox function creates, displays, and operates a message box.
The message box contains an application-defined message and title,
plus any combination of predefined icons and push buttons.
int MessageBox(
HWND hWnd, // handle of owner window
LPCTSTR lpText, // address of text in message box
LPCTSTR lpCaption, // address of title of message box
UINT uType // style of message box
);
HWND hWnd, // handle of owner window
LPCTSTR lpText, // address of text in message box
LPCTSTR lpCaption, // address of title of message box
UINT uType // style of message box
);
This is all you need to know about the MessageBox.
Now its time to do something with the CodeCaves.
At first to use the MessageBox we need to create some text for output it on the
MessageBox. In the following picture I've selected some lines of the CodeCaves and
highlighted the BinaryEdit menu for you.
If you pressed on Binary=>Edit or (CTRL+E) you will see following window.
Just fill it out like me if you want.
Press OK and you'll see the modified code in red:
Press now CTRL+A to reanalyze the code.
OK! If you want to have a different MessageBox Caption than the title you can repeat this
step to make a second ASCII like the "INJECTED NOTEPAD".
-Some ASM-
Now its time for some ASM ;)
We need to invoke a MessageBox from ASM. This is quite simple! PUSH 0 ; BUTTONS = <OK ONLY>
PUSH 1008751 ; CAPTION = Our adress of the "INJECTED NOTEPAD"
PUSH 1008751 ; MESSAGE = Same like above.
PUSH 0 ; ICON = <NO ICON>
CALL MessageBoxA; Run MessageBoxA with the Params above.
This few lines entered in Olly should look like this:
Do you see the arrow?! THIS IS NOW A VERY IMPORTANT STEP!
If we save it now and run it you will NOT see any effect. Why?
Because our litte routine is not called yet!
You need to write down the Offset of your first "PUSH 0" because we
need to make a jump from the programs origin to here and back again ;)
If you noted the offset of the first PUSH down, goto the origin of the program like below.
Now its time for some ASM ;)
We need to invoke a MessageBox from ASM. This is quite simple! PUSH 0 ; BUTTONS = <OK ONLY>
PUSH 1008751 ; CAPTION = Our adress of the "INJECTED NOTEPAD"
PUSH 1008751 ; MESSAGE = Same like above.
PUSH 0 ; ICON = <NO ICON>
CALL MessageBoxA; Run MessageBoxA with the Params above.
This few lines entered in Olly should look like this:
Do you see the arrow?! THIS IS NOW A VERY IMPORTANT STEP!
If we save it now and run it you will NOT see any effect. Why?
Because our litte routine is not called yet!
You need to write down the Offset of your first "PUSH 0" because we
need to make a jump from the programs origin to here and back again ;)
If you noted the offset of the first PUSH down, goto the origin of the program like below.
Now you're at the FIRST line of code which will be executed.
Do you remember that the first thing we wanted to do is to run our code? :)
Yehaa! We're on the right way!
Select now from the origin some lines and copy it into the Clipboard.
Paste the clipboard into a texteditor and leave them there. We need this lines later.
If you have pasted it go to the first line of the program.
(In the picture upper it's the PUSH 70).
Double click on it and enter in the box "JMP <adress of your first push>"
Press on Assemble and you will the the again the red marked(patched) code.
Do you remember that the first thing we wanted to do is to run our code? :)
Yehaa! We're on the right way!
Select now from the origin some lines and copy it into the Clipboard.
Paste the clipboard into a texteditor and leave them there. We need this lines later.
If you have pasted it go to the first line of the program.
(In the picture upper it's the PUSH 70).
Double click on it and enter in the box "JMP <adress of your first push>"
Press on Assemble and you will the the again the red marked(patched) code.
Look to the redbox! This is the address we need to jump to after our injected code.
If we jump here after the injection the program will execute like without our injection :)
But there is one thing we need to do at least!
Compare the "new" origin with the old one you've pasted into a clipboard.
You will see that there are a few lines overwritten! But this lines are needed to run
the programm without errors. Identify the lines which get overwritten.
In my case the overwritten lines are: PUSH 70
PUSH NOTEPAD.01001898
Click on the first line (our JMP) and press ENTER.
You'll dropped to your MessageBox invokation!
After our CALL MessageBoxA we need to insert now the overwritten lines AND the jump back!
NOW you're done!
(If you want to test the "JumpBack"-Jump just select it and press ENTER.
If you get to the right line you can be sure that's ok! If not check Offset!) To save the "new" Notepad take a look the the following picture:
If you press on "All modifications" a new little window will be shown.
Press on "Copy All" on this window.
A new window with the new ASM code will be shown.
Close the new window (THE CHILD WINDOW! NOT OLLY DBG WINDOW!).
Then a save dialog let you choose a new filename.
Save the file and run it. If you're successful you will get this result:
Press on OK and Notepad will start normally ;)
If we jump here after the injection the program will execute like without our injection :)
But there is one thing we need to do at least!
Compare the "new" origin with the old one you've pasted into a clipboard.
You will see that there are a few lines overwritten! But this lines are needed to run
the programm without errors. Identify the lines which get overwritten.
In my case the overwritten lines are: PUSH 70
PUSH NOTEPAD.01001898
Click on the first line (our JMP) and press ENTER.
You'll dropped to your MessageBox invokation!
After our CALL MessageBoxA we need to insert now the overwritten lines AND the jump back!
NOW you're done!
(If you want to test the "JumpBack"-Jump just select it and press ENTER.
If you get to the right line you can be sure that's ok! If not check Offset!) To save the "new" Notepad take a look the the following picture:
If you press on "All modifications" a new little window will be shown.
Press on "Copy All" on this window.
A new window with the new ASM code will be shown.
Close the new window (THE CHILD WINDOW! NOT OLLY DBG WINDOW!).
Then a save dialog let you choose a new filename.
Save the file and run it. If you're successful you will get this result:
Press on OK and Notepad will start normally ;)
-Last Words- DO NOT abuse debuggers to attach shellcodes or things like that into EXEs!
Just lern and understand!
Greets to: All students from the FH-BRS!
Just lern and understand!
Greets to: All students from the FH-BRS!
Autor: Iman Karim
Email: iman.karim@smail.inf.fh-bonn-rhein-sieg.de

This post was written by: Franklin Manuel
Franklin Manuel is a professional blogger, web designer and front end web developer. Follow him on Twitter
Subscribe to:
Post Comments (Atom)

















0 Responses to “How to inject code into a exe file”
Post a Comment